- Configurar Vpn Client To Gateway Cisco Rv042
- Client To Gateway Vpn Rv042 Settings
- Configurar Vpn Rv042 Client To Gateway
- Client To Gateway Vpn Rv042 Review
Objective
- Page 69: Appendix C: Gateway-To-Gateway Vpn Tunnel Appendix C Gateway-to-Gateway VPN Tunnel Appendix C: Configuration of the RVL200 Gateway-to-Gateway VPN Follow these instructions for the first VPN Router, designated RVL200. The other VPN Router is designated Tunnel the RV042. Launch the web browser for a networked computer, designated PC 1.
- Click the Add Now button to see the Gateway to Gateway screen, Figure 44. Client to Gateway: Figure 43 shows the Client to Gateway tunnel. A tunnel created between the VPN Router and the Client user which using VPN client software that supports IPSec. Click the Add Now button to see the Client to Gateway screen, Figure 45.
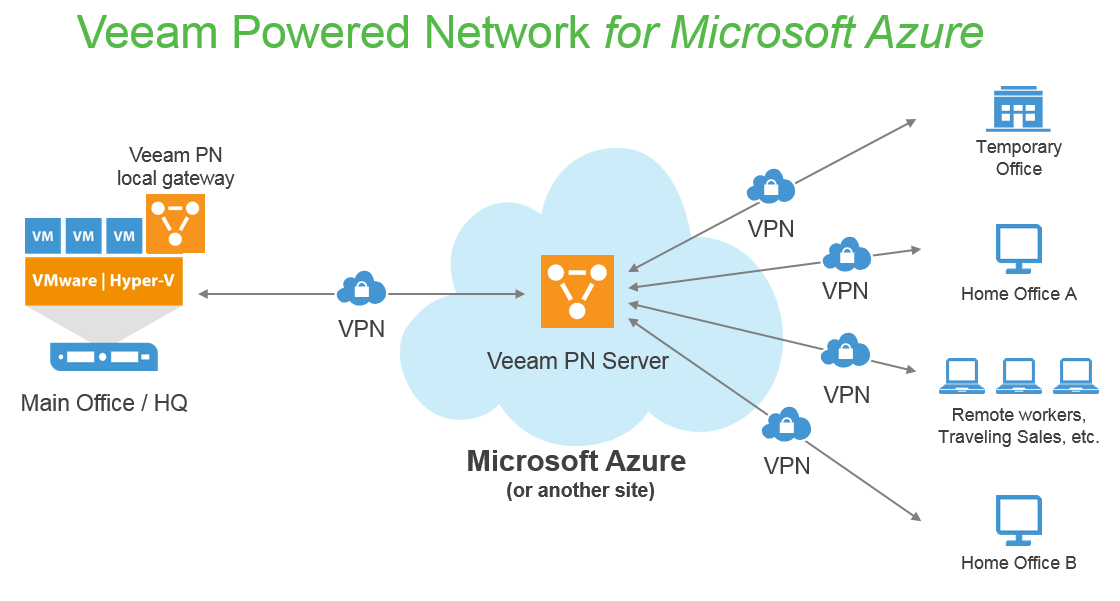
This article explains how to configure remote access Virtual Private Network (VPN) tunnel from client to gateway on RV016, RV042, RV042G and RV082 VPN Routers with the help of third party VPN client software as The Green Bow or VPN Tracker.
Am Using the Cisco RV 042 VPN Router. Can anyone tell what free client to use to connect to the VPN of Cisco RV042? I want to use the Client to Gateway and also need to have a Fix IP for the VPN User. I tried the cisco free Client and it just can not connect despite the right user name and Password and having the certificate also. Finding a VPN solution that is right for Client To Gateway Vpn Rv042 you can be challenging. There are a lot of options available and many factors you need to consider before making a decision. In this VPNSecure vs VPN Unlimited comparison, we're going to compare these two.
Introduction
A VPN is a private network that is used to virtually connect devices of the remote user through the public network to provide security. Remote access tunnel VPN is the process used to configure a VPN between a client computer and a network. The client is configured in the desktop or laptop of the users through VPN client software. It provides the users to securely connect with the network remotely. Client to gateway VPN connection is useful for the remote employees to connect to the office network remotely and securely.
Applicable Devices
- RV016
- RV042
- RV042G
- RV082
Software Version
- v4.2.2.08
Configure a VPN Tunnel
Step 1. Log in to the web configuration utility and choose VPN > Client to Gateway. The Client to Gateway page opens:
Add a New Tunnel
Step 1. Click the appropriate radio button according to what kind of tunnel you want to add.
- Tunnel - Represents a tunnel for a remote single user.
- Group VPN - Represents a tunnel for a remote group of users.
The Tunnel Number is an automatically generated field that displays the number of the tunnel.
Step 2. Enter a name for the tunnel in the Tunnel Name field.
Step 3. Choose the appropriate WAN interface to use for the VPN tunnel from the Interface drop-down list.
Step 4. (Optional) To enable the VPN, check the check box in the Enable field. By default it is always checked.
Local Group Setup
Step 1. Choose the appropriate router identification method to establish a VPN tunnel from the Local Security Gateway drop-down list. Skip this step if you chose Group VPN in Step 1 of the Add A New Tunnel section.
- IP Only - Access to the tunnel is possible through a static WAN IP address. You can choose this option only if the router has a static WAN IP. The static WAN IP address appears automatically.
- IP + Domain Name(FQDN) Authentication - Access to the tunnel is possible through a static IP address and a registered Fully Qualified Domain Name (FQDN) domain. The static WAN IP address is an auto generated field.
- IP + E-mail Address(USER FQDN) Authentication - Access to the tunnel is possible through a static IP address and an email address. The static WAN IP address is an auto generated field.
- Dynamic IP + Domain Name(FQDN) Authentication - Access to the tunnel is possible through a dynamic IP address and a registered domain.
- Dynamic IP + E-mail Address(USER FQDN) Authentication — Access to the tunnel is possible through a dynamic IP address and an email address.
Step 2. Enter the name of the registered Fully Qualified Domain in the Domain Name field if you choose IP + Domain Name (FQDN) Authentication or Dynamic IP + Domain Name (FQDN) Authentication in Step 1.
Step 3. Enter the Email Address in the Email Address field if you choose IP + E-mail Address(USER FQDN) Authentication or Dynamic IP + E-mail Address(USER FQDN) Authentication in Step 1.
Step 4. Choose the appropriate local LAN user or group of users who can access the VPN tunnel from the Local Security Group drop-down list. The default is Subnet.
- IP - Only one specific LAN device can access to the tunnel. If you choose this option, enter the IP address of the LAN device in the IP Address field. The default IP is 192.168.1.0.
- Subnet - All LAN devices on a specific subnet can access to the tunnel. If you choose this option, enter the IP address and subnet mask of the LAN devices in the IP Address and Subnet Mask field respectively. The default mask is 255.255.255.0.
- IP Range - A range of LAN devices can access to the tunnel. If you choose this option, enter the starting and ending IP address in the Begin IP and End IP fields respectively. The default range is from 192.168.1.0 to 192.168.1.254.
Step 5. Click Save to save the settings.
Remote Client Setup
Step 1. If you choose Tunnel, choose the appropriate client identification method to establish a VPN tunnel from the Remote Security Gateway Type drop-down list. The default is IP Only. Skip this step if Group VPN in Step 1 of the Add A New Tunnel section was chosen.
- IP Only - Access to the tunnel is possible through the static WAN IP of the client only. You must know the static WAN IP of the client to use this option.
- IP + Domain Name(FQDN) Authentication - Access to the tunnel is possible through a static IP address of the client and a registered domain.
- IP + E-mail Address(USER FQDN) Authentication - Access to the tunnel is possible through a static IP address of the client and an email address.
- Dynamic IP + Domain Name(FQDN) Authentication - Access to the tunnel is possible through a dynamic IP address of the client and a registered domain.
- Dynamic IP + E-mail Address(USER FQDN) Authentication - Access to the tunnel is possible through a dynamic IP address of the client and an email address.
Step 2. Enter the IP address of the remote client in the IP Address field if you chose IP Only, IP + Domain Name (FQDN), or IP + E-mail Address (User FQDN) Authentication in Step 1.
Step 3. Choose the appropriate option from the drop-down list to enter the IP address if you know it or resolve the IP address from the DNS server if you choose IP Only or IP + Domain Name (FQDN) Authentication or IP + E-mail Address(USER FQDN) Authentication in the Step 1.
- IP Address - Represents the static IP address of the remote client. Enter the static IP address in the field.
- IP by DNS Resolved - Represents the domain name of the IP address which retrieves the IP address automatically through the local DNS server if you do not know the static IP address of the remote client. Enter the domain name of the IP address in the field.
Step 4. Enter the domain name of the IP address in the Domain name field if you choose IP + Domain Name (FQDN) Authentication or Dynamic IP + Domain Name (FQDN) Authentication in Step 1.
Step 5. Enter the email address in the Email Address field if you choose IP + E-mail Address(USER FQDN) Authentication or Dynamic IP + E-mail Address(USER FQDN) Authentication in Step 1.
Step 6. If you choose Group, choose the appropriate remote client type from the Remote Client drop-down list. Skip this step if Tunnel VPN in Step 1 of the Add A New Tunnel section was chosen.
- Domain Name (FQDN) - Access to the tunnel is possible through a registered domain. If you choose this option, enter the name of the registered Domain in the Domain Name field.
- E-mail Addr.(USER FQDN) - Access to the tunnel is possible through an email address of the client. If you choose this option, enter the Email Address in the Email Address field.
- Microsoft XP/2000 VPN Client - Access to the tunnel is possible through Microsoft XP or Microsoft 2000 windows software. Remote users with Microsoft VPN client software can access to the tunnel through the software.
Step 7. Click Save to save the settings.
IPSec Setup
Internet Protocol Security (IPSec) is an internet layer security protocol which provides end-to-end security through authentication and encryption during any communication session.
Note: Two ends of the VPN need to have the same methods of encryption, decryption and authentication for the IPSec to work. Also the Perfect Forward Secrecy key must be same on the both side of the tunnel.
Step 1. Choose the appropriate mode of key management to ensure security from the Keying Mode drop-down list. The default mode is IKE with Preshared key.
- Manual - A custom security mode to generate a new security key by yourself and no negotiation with the key. It is the best to use during troubleshooting and small static environment. If you choose Group VPN in Step 1 in Add A New Tunnel section, this option is disabled.
- IKE with Preshared key - Internet Key Exchange (IKE) protocol is used to automatically generate and exchange a preshared key to establish authenticate communication for the tunnel.
Manual Key Mode Configuration
Step 1. Enter the unique hexadecimal value for incoming Security Parameter Index (SPI) in the Incoming SPI field. SPI is carried in Encapsulating Security Payload Protocol (ESP) header which together determine the protection for the incoming packet. You can enter from 100 to ffffffff. The incoming SPI of the local router need to match with the outgoing SPI of the remote router.
Step 2. Enter the unique hexadecimal value for outgoing Security Parameter Index (SPI) in the Outgoing SPI field. SPI is carried in Encapsulating Security Payload Protocol (ESP) header which together determine the protection for the outgoing packet. You can enter from 100 to ffffffff. The outgoing SPI of the remote router need to match with the incoming SPI of the local router.
Step 3. Choose the appropriate encryption method for the data from the Encryption drop-down list. The recommended encryption is 3DES. The VPN tunnel needs to use the same encryption method for both ends.
- DES - Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
- 3DES - Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
Step 4. Choose the appropriate authentication method for the data from the Authentication drop-down list. The recommended authentication is SHA1 as it is more secure than MD5. The VPN tunnel needs to use the same authentication method for both ends.
- MD5 - Message Digest Algorithm-5 (MD5) represents 32 digit hexadecimal hash function which provides protection to the data from malicious attack by the checksum calculation.
- SHA1 - Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
Step 5. Enter the key to encrypt and decrypt data in the Encryption Key field. If you choose DES as encryption method in Step 3, enter a 16 digit hexadecimal value. If you choose 3DES as encryption method in Step 3, enter a 40 digit hexadecimal value.
Step 6. Enter a pre-shared key to authenticate the traffic in Authentication Key field. If you choose MD5 as authentication method in step 4, enter 32 digit hexadecimal value. If you choose SHA as authentication method in Step 4, enter 40 digit hexadecimal value. The VPN tunnel needs to use the same preshared key for both of its ends.
Step 7. Click Save to save the settings.
IKE with Preshared Key Mode Configuration
Step 1. Free itunes store download. Choose the appropriate Phase 1 DH Group from the Phase 1 DH Group drop-down list. Phase 1 is used to establish the simplex, logical security association (SA) between the two ends of the tunnel to support secure authenticate communication. Diffie-Hellman (DH) is a cryptographic key exchange protocol which is used to determine the strength of the key during Phase 1 and it also shares the secret key to authenticate the communication.
- Group 1 - 768 bit - The lowest strength key and the most insecure authentication group. But it takes less time to compute the IKE keys. This option is preferred if the speed of the network is low.
- Group 2 - 1024 bit - The higher strength key and more secure authentication group. But it needs some time to compute the IKE keys.
- Group 5 - 1536 bit - Represents the highest strength key and the most secure authentication group. It needs more time to compute the IKE keys. It is preferred if the speed of the network is high.
Step 2. Choose the appropriate Phase 1 Encryption to encrypt the key from the Phase 1 Encryption drop-down list. 3DES is recommended as it is the most secure encryption method. The VPN tunnel needs to use the same encryption method for both of its ends.
- DES - Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
- 3DES - Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
- AES-128 - Advanced Encryption Standard (AES) is 128 bit encryption method which transforms the plain text into cipher text through 10 cycles repetitions.
- AES-192 - Advanced Encryption Standard (AES) is 192 bit encryption method which transforms the plain text into cipher text through 12 cycles repetitions. AES-192 is more secure than AES-128.
- AES-256 - Advanced Encryption Standard (AES) is 256 bit encryption method which transforms the plain text into cipher text through 14 cycles repetitions. AES-256 is the most secure encryption method.
Step 3. Choose the appropriate Phase 1 authentication method from the Phase 1 Authentication drop-down list. The VPN tunnel needs to use the same authentication method for both of its ends.
- MD5 - Message Digest Algorithm-5 (MD5) represents 32 digit hexadecimal hash function which provide protection to the data from malicious attack by the checksum calculation.
- SHA1 - Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
Step 4. Enter the amount of time in seconds that the Phase 1 keys are valid and the VPN tunnel remains active in the Phase 1 SA Life Time field.
Step 5. Check the Perfect Forward Secrecy check box to provide more protection to the keys. This option allows the router to generate a new key if any key is compromised. The encrypted data is only compromised through the compromised key. Autofill after effects project. So it provides more secure and authenticate communication as it secures other keys though a key is compromised. This is a recommended action as it provides more security.
Step 6. Choose the appropriate Phase 2 DH Group from the Phase 2 DH Group drop-down list. Phase 2 uses security association and it is used to determine the security of the data packet during the data packets pass through the two end points.
Step 7. Choose the appropriate Phase 2 Encryption to encrypt the key from the Phase 2 Encryption drop-down list. AES-256 is recommended as it is the most secure encryption method. The VPN tunnel needs to use the same encryption method for both of its ends.
- DES - Data Encryption Standard (DES) uses a 56-bit key size for data encryption. DES is outdated and should be only used if one endpoint only supports DES.
- 3DES - Triple Data Encryption Standard (3DES) is a 168 bit, simple encryption method. 3DES encrypts the data three times, which provides more security then DES.
- AES-128 - Advanced Encryption Standard (AES) is 128 bit encryption method which transforms the plain text into cipher text through 10 cycles repetitions.
- AES-192 - Advanced Encryption Standard (AES) is 192 bit encryption method which transforms the plain text into cipher text through 12 cycles repetitions. AES-192 is more secure than AES-128.
- AES-256 - Advanced Encryption Standard (AES) is 256 bit encryption method which transforms the plain text into cipher text through 14 cycles repetitions. AES-256 is the most secure encryption method.
Step 8. Choose the appropriate authentication method from the Phase 2 Authentication drop-down list. The VPN tunnel needs to use the same authentication method for both ends.
- MD5 - Message Digest Algorithm-5 (MD5) represents 32 digit hexadecimal hash function which provide protection to the data from malicious attack by the checksum calculation.
- SHA1 - Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
- Null - No authentication method is used.
Step 9. Enter the amount of time in seconds that the Phase 2 keys are valid and the VPN tunnel remains active in the Phase 2 SA Life Time field.
Step 10. Enter a key which is shared previously between the IKE peers to authenticate the peers in the Preshared Key field. Up to 30 hexadecimal and character can be used as the preshared key. The VPN tunnel needs to use the same preshared key for both of its ends.
Note: It is strongly recommended to frequently change the preshared key between the IKE peers so the the VPN remains secured.
Step 11. Check the Minimum Preshared Key Complexity check box if you want to enable strength meter for the preshared key. It is used for determine the strength of the preshared key through color bars
Note: Preshared Key Strength Meter shows the strength of the preshared key through colored bars. Red indicates weak strength, yellow indicates acceptable strength and green indicates strong strength.
Step 12. Click Save to save the settings.
Advanced IKE with Pre-shared Key Mode Configuration
Step 1. Click Advanced to display the advanced settings for IKE with Preshared key.
Step 2. Check the Aggressive Mode check box if your network speed is low. This exchanges the IDs of the end points of the tunnel in clear text during SA connection (Phase 1), which requires less time to exchange but is less secure.
Note: Aggressive Mode is not available for group client to gateway VPN connection.
Step 3. Check the Compress (Support IP Payload Compression Protocol (IPComp)) check box if you want to compress the size of the IP datagrams. IPComp is an IP compression protocol which is used to compress the size of IP datagram. IP compression is useful if the network speed is low and the user wants to quickly transmit the data without any loss through the slow network, but it does not provide any security.
Step 4. Check the Keep-Alive check box if you always want the connection of the VPN tunnel remain active. Keep Alive helps to re-establish the connections immediately if any connection becomes inactive.
Step 5. Check the AH Hash Algorithm check box if you want to enable Authenticate Header (AH). AH provides authentication to origin data, data integrity through checksum and protection into the IP header. The tunnel should have the same algorithm for both of its sides.
- MD5 - Message Digest Algorithm-5 (MD5) represents 128 digit hexadecimal hash function which provides protection to the data from malicious attack by the checksum calculation.
- SHA1 - Secure Hash Algorithm version 1 (SHA1) is a 160 bit hash function which is more secure than MD5 but it takes more time to compute.
Step 6. Check NetBIOS Broadcast if you want to allow non-routable traffic through the VPN tunnel. The default is unchecked. NetBIOS is used to detect network resources like printers, computers etc. in the network through some software applications and Windows features like Network Neighborhood.
Step 7. Check NAT Traversal check box if you want to access to the internet from your private LAN through a public IP address. If your VPN router is behind a NAT gateway, check this check box to enable NAT traversal. Both ends of the tunnel must have the same settings.
Step 8. Check Dead Peer Detection Interval to check the liveliness of the VPN tunnel through hello or ACK in a periodic manner. If you check this check box, enter the desired duration or interval of the hello messages.
Note: You can configure Dead Peer Detection Interval only for single client to gateway VPN connection, not for group client to gateway VPN connection.
Step 9. Click Save to save the settings.
You have now learned how to configure remote access VPN tunnel from client to gateway on RV016, RV042, RV042G and RV082 VPN routers.
Configurar Vpn Client To Gateway Cisco Rv042
Similar Messages:
ADVERTISEMENT
Linksys Wired Router :: RV042 Gateway To Gateway Connection?
Feb 8, 2011we do have 2 Rv042, one in my office and one in my house. in the office we do have static ip and at home none. question is can i connect the two RV042?
Linksys Wired Router :: RV042 - Gateway To Gateway VPN Connection
Mar 22, 2011I have some problems in my network with Gateway to Gateway Vpn Connection using two Rv042 routers.
I cannot ping the computers with static ip configuration.
In local an remote computers who have DHCP ip configuration i can ping each other .
Linksys Wired Router :: RV042 / Setup A Vpn Gateway To Gateway
Apr 6, 2013i am trying to setup a vpn Gateway To Gateway when i setup the vpn i can ping the 2 rv042 i cant see any computer in the network places when there comect we need to see the computer in the network places so are pos will run?
Linksys Wired Router :: RV042 - Can't Access Internet Or Ping Gateway
Jan 4, 2011I am using the default configuration at this point. I just connected 1 computer using the default IP with DHCP on the RV042 router. 192.168.1.0/255.255.255.0.I connect my wildblue satalite modem using a static IP address 75.106.203.xxx / 255.255.252.0 I can ping the RV042 router and the static IP address of the wildblue router but I can't ping the gateway on the wildblue side. Either from the PC or the Router diag tools.
Linksys Wired Router :: Using RV042 As Layer 3 Clear Gateway For Comcast EDI?
Feb 7, 2013Comcast installed a new fiber 10M EDI internet connection in our facility the other day and found out it is our responsibility to provide a layer 3 gateway to map the internet connection to the 14 public IP addresses they assigned to us. We are using RV042 for our existing networks with a T1 we had.
Will the RV042 provide the gateway function to route the single IP address comcast provided to the 15 public IP addresses? If so , can you provide the configuration example on this process?
Comcast EDI Connection ---> ???????? ----> 14 Static External Addresses
Interconnect Block 51.235.227.60 / 255.255.255.252.Comcast Gateway is 51.235.227.61Clear Layer 3 device WAN interface: 51.235.227.62Usable IP Block 51.235.227.96/28Mask: 255.255.255.240Usable Addresses: 51.235.227.97 - 51.235.227.110
Linksys Wired Router :: RV082 Gateway To Gateway VPN Not Connecting?
Jan 24, 2012I recently swapped out an RV082 with a newer model (still RV082 but black and a different interface). I configured the Gateway to Gateway VPN exactly as it was before but none of the three other RV082's will connect. I have tried deleting the connections several times to no avail. I have aggressive mode disabled and have tried with the firewall on and off. Below are the settings (IP's have been X'd out) and the log.
Settings:
IP OnlyIP Address : X0X.X0X.20.31Local Security Group Type : IPSubnetIP RangeIP Address : Subnet Mask : Remote Group Setup
Remote Security Gateway Type : IP OnlyIP AddressIP by DNS Resolved : Remote Security Group Type : IPSubnetIP RangeIP Address : Subnet Mask : AES-192AES-256AES-128 AES-192AES-256 AES-128 IPSec Setup3DES Keying Mode : ManualIKE with Preshared keyPhase 1 DH Group : Group 1 - 768 bitGroup 2 - 1024 bitGroup 5 - 1536 bitPhase 1 Encryption : DES Phase 1 Authentication : MD5SHA1Phase 1 SA Life Time : secondsPerfect Forward Secrecy : Phase 2 DH Group : Group 1 - 768 bitGroup 2 - 1024 bitGroup 5 - 1536 bitPhase 2 Encryption : NULLDES3DES Phase 2 Authentication : NULLMD5SHA1Phase 2 SA Life Time : secondsPreshared Key : Minimum Preshared Key Complexity : EnableLOG:
[code]...
Linksys Wired Router :: RV082 Gateway 2 Gateway VPN Can't Ping
Jul 26, 2012We have a VPN setup between two Cisco RV082 routers, the VPN status shows as connected however I can't ping the other network. I am unable to ping between routers, let alone ping computers behind those routers.
We have 2 branches, branch 1 is on a static IP and branch 2 is Dynamic. I am able to connect via QuickVPN from Branch 2 to Branch 1 and remote desktop to computers, however have yet to VPN/remote desktop in the opposite direction.
To me it seems like a firewall issue at branch 2, but what's causing this. Also they are currently running 2 differnet firmware version not sure if this would cause a problem.
Linksys Wired Router :: RV0XX Gateway To Gateway VPN?
Mar 6, 2011I have an RV082 and a RV042. I have been able to successfully establish a gateway to gateway vpn connection between them both, and I can remotely administer each router through the VPN connection, but I am unable to ping computers from one side of the connection to the other. For example, a computer in the 10.10.1.0 subnet can't see / ping / communicate with a computer in the 192.168.1.0 subnet.
Below are the configurations for each. Aside from the static IP configurations and the VPN configurations, no other changes were made to the routers. RV082 DHCP Enabled Tunnel Status: Connected Local Group Setup
IP Only: X.X.X.66Local Security Group Type: SubnetIP Address: 10.10.1.0Subnet Mask: 255.255.255.0Remote Group Setup
Linksys Wired Router :: Should Set RV042 Up As Gateway Or As Router
Aug 8, 2011I am setting up an RV042 for my small business office and I am trying understand how it needs to be configured.
-For WAN1 I have a Wildblue Satellite Modem connected IP 70.66.93.4
-For WAN2 I have a Cradlepoint CTR35 Router with a verizon AirCard Connected IP 192.168.0.1
(Verizon has a 5GB download limit and wildblue has a 17GB download limit but it drops out in poor weather)The LAN is IP 172.16.0.1 Subnet Mask 255.255. 255. 0Should I set the RV042 up as a gateway or as a router?
Cisco Security :: Rv042 Vpn Openswan Gateway To Gateway Linux Unbutu
Sep 13, 2012config setup
protostack=netkey
klipsdebug=none
[Code]..
Cisco Routers :: RV042 Gateway To Gateway Tunnels Not Reconnecting
Apr 11, 2013I have two Cisco RV042 Routers, they are being used to connect two offices, i have created a standard gateway to gateway connection, fixed public ip addresses on both sides and everything works fine, except when the tunnel gets disconnected, it does not connect back automatically, i have to log into either router console and click the connect button to get the tunnel working again, this is really annoying since it happens once or twice a day at least.
Linksys Wired Router :: RV082 Gateway Shows No Loss On Packet
Mar 25, 2011I have RV082 in many locations and it is working fine.One location I just starting to have problem with packet lose (50 to 60 %)I ping between two location which i am having problem.Gateway to Gateway shows no lose on packet (reply with 20ms avg.)but router to router will lose packet 50 to 60 %.
Linksys Wired Router :: Can't Set RV016 To Assign A Default Gateway IP Of Server
Jun 22, 2011I am using a RV016 (192.168.1.2) as a router and DHCP. It automatically assigns its own IP which is 192.168.1.2. I can not set my RV016 to assign a Default Gateway IP of the server. The workstations will connect to internet via this server (192.168.1.1)
Linksys Wired Router :: BEFSR41 V4.3 / Error - Wrong Gateway Input After Firmware Upgraded
Aug 14, 2011I have upgraded the firmware on my Linksys BEFSR41 V4.3 router. On this router i used Statis IP (so DHCP enabled). This worked fine on my network, until this upgrade. Now when i try to ad another static IP , or when i want to change something in the Routing-tab, i get this message ' Wrong Gateway Input! It should be the same subnet with WAN IP'. Strange because i haven't changed anything in the settings.I already did a complete reset on the router, still the same problem.
Cisco VPN :: Linksys WRT54G To RV042 (Client To Gateway) Access
Client To Gateway Vpn Rv042 Settings
Apr 12, 2011We recently upgraded from a Linksys WRT54G router to a Cisco RV042 to gain 'gateway-to-gateway' automated VPN access. However, we are unable to get 'client to gateway' access working.
With the Linksys WRT54G we used a 'username' 'password' pair for remote client authenication. This worked for both Windows and Mac OS X users using the built-in PPTP client. We found we had to set 'encryption' value to 'none' on the client side.
I am confused by the setup screens on the RV042. It looks like I must setup a 'tunnel' (VPN->Client to Gateway), there is (VPN->VPN Client Access) where I can enter a username/password, and also (VPN->PPTP Server) where another username/password pair can be entered. I have tried all sorts of combinations but 'no love'. I am particularly mystified by the (VPN->Client to Gateway) settings for 'Remote Client Setup'; the client can be calling in from anywhere and there is an option for 'Dynamic IP + Email Address' but I'm not sure how that maps onto the client (do they use the email address as their account name?). I have also looked at defining a 'Group VPN' where I am given other options. But nothing works from the client.
I just need to come up with some setup that works, that I can document to both PC and Mac users at a miniumum.
Cisco Routers :: Quickvpn / Client To Gateway Vpn Rv042 Can Only Ping Router?
Jan 27, 2012I am setting up remote access using an RV042 router. Using quickvpn or a client-to gateway vpn and shrewsoft client, I can only access/ping the LAN side of the remote router and one machine on the remote network. The PPTP server and native Windows 7 connection provide access to all machines on the remote network.I have 2 possible reasons for this and would like to find the real reason:
1) The remote RV042 is behind another router, and that router restricts access other than the PPTP traffic.
2) The VPN tunnels other than PPTP only allow access to the remote LAN side of the router and remote machines that have the remote router defined as their gateway in the IP configuration.
Constantly Dropping Offline With Default Gateway Message On Windows 7
Mar 21, 2011I installed Windows 7 a few weeks back with no hitches but over the last week I have been getting regularly kicked off line with above message that the default gateway was not available! Fortunately the Windows troubleshooter fixes it every time but intrigued why it keeps happening.I have reset the adaptor and the router but still no luck!
Cisco :: OSPF - Router As A Gateway And Has An Own Gateway?
Jan 29, 2013Can a router using OSPF propagate that he is a router with default-information originate.. at the same time when he got an own gateway of last resort to an IP-adress? If so, how? I can't get it to work.
Gateway 2wire 3800 HGV-B Router - Wireless Working Properly But Wired Isn't?
Jul 22, 2012I've got a Gateway 2wire 3800 HGV-B router which works fine wirelessly, but when using an ethernet cable to connect to the internet, it doesn't even recognize the computer. My laptop runs wirelessly all the time, and I recently picked up a desktop PC for home here, and it's the first wired connection I'm using, but for some reason the wired connection isn't connecting to my network, but instead it's own Unidentified Network.
Cisco Routers :: RV042 502 Bad Gateway CGI Was Not CGI / 1.1 Compliant
Mar 31, 2013I've got half a dozen RV042 routers in various locations. They are running v4.0.0.07. Seemingly randomly, I got the 502 Bad GatewayThe CGI was not CGI/1.1 compliant. error when attempting to log into the web interface with google chrome (same with IE too). This happens from the LAN side. I actually didn't notice it until my Opsview monitoring software threw up a critical when it didn't get an http response. The router is otherwise actually working just fine.Since the first occurrence, more of my routers have developed the same error.
I've tried different browsers, clearing caches, though I'm not surprised those efforts were fruitless, as there is clearly a problem even when no browser is involved (nagios). The nagios http check also returns a 502 Bad Gateway.
Cisco VPN :: QuickVPN - Gateway Not Responding - RV042?
Oct 28, 2011I'm running Cisco QuickVPN on a clients laptop (Windows 7). Windows firewall is disabled because McAfee SaaS is running.I sometimes have the issue that the initial connection attempt comes back with 'Gateway not respoding' during the network verification process. You close the program, you open it again and it works. Sometimes it takes 2 or 3 tries. Today I have the issue that my client tried it like 20 times including several reboots and it's just not working. I tried it from my own computer and it connected fine on the 2nd try.I'm thinking that it might be time-out thing, that the VPN client doesn't receive a response fast enough? I know my clients home internet is darn slow.
Configurar Vpn Rv042 Client To Gateway
Cisco VPN :: RV042 Establish VPN Gateway Connection
May 31, 2012I have successfully connected two RV042s to establish a VPN gateway to VPN gateway connection. I have the follow questions:
1. I would like to keep the VPN tunnel connection time indefinite. Is it sufficient by checking the 'Keep-Alive' box on the VPN -> Gateway To Gateway -> Advance page? Or, I have to ping the RV042 periodically?
2. Do the 'Phase 1/Phase 2 SA Life Time' (on VPN -> Gateway To Gateway page) settings have any impact on keeping the VPN connection time indefinite? What are the optimal values for them?
3. Is there an API, command, or script to replace a manual clicking on the 'CONNECT' button to establish the VPN tunnel from the VPN -> Summary page? Or, is there a way to accomplish this at power up?
4. Is there a way to establish a VPN tunnel without going through login and clicking the 'CONNECT' button? (Auto connect at power up?)
Cisco Routers :: Set Up RV042 As VPN Gateway For Client
Aug 29, 2011I set up an RV042 as a VPN gateway for a client a year ago. It is running firmware 1.3.12.19-tm (Feb 13 2009 13:03:21). I created a new certificate. When I download the client certificate, It comes as a .zip file. One the can not be opened by a zip utlity (windows, Winzip or 7 zip). It looks like I can just rename the file to a .pem file, but I want to make sure that is right. They were getting QuickVPN timeouts, but that looks like it was fixed in 1.3.13.
Cisco Routers :: RV042 Not As Default Gateway?
Apr 11, 2012I have RV042 on my remote network, i have problems with VPN connection , user can connect to RV042 but only inside IPs that can ping from vpn user.Is it any way to make the traffic from Rv042 will back to RV042 . maybe with nat. in example below 192.168.5.100 is my lan IP from my DSL dhcp, and 172.27.0.20 ip on remote, traffic not back to my pc/vpn client, what i want is to translate 192.168.5.100 to RV042 LAN ip address
1485: ICMP echo request (len 32 id 256 seq 29) 192.168.5.100 > 172.27.0.20
1486: ICMP echo reply (len 32 id 256 seq 29) 172.27.0.9 > 192.168.5.100
1487: ICMP echo request (len 32 id 256 seq 30) 192.168.5.100 > 172.27.0.20
1488: ICMP echo reply (len 32 id 256 seq 30) 172.27.0.9 > 192.168.5.100
[code]..
Cisco Routers :: RV082 Gateway To Gateway VPN Not Resolving Remote DynDns
Feb 14, 2013I've got two RV082's connected. Each has a dynamic IP (changes typically every few weeks). I've configured the tunnels on both ends with a local and remote 'Remote/Local Security Gateway Type' of 'Dynamic IP + Domain Name(FQDN) Authentication'.If I look at the VPN Summary tunnel status, it shows an IP address of 'mydomain.dyndns.org 0.0.0.0' under the 'Remote Gateway' column heading. The Tunnel Test 'Connect' button is N/A.I can resolve both of the mydomain.dyndns.org entries on both sides of each VPN using the Diagnostic DNS lookup tool within each router. If I hardwire a fixed IP address for the Local and Remote Gateway everything works just fine. VPN is good.
I just can't seem to get the 'mydomain.dyndns.org' function to work. It appears the router can't resolve the dynamic IP from the domain names on each of the routers.
Cisco Routers :: How To Manage Port 80 Hosts Via Gateway To Gateway VPN (rv220w)
Aug 30, 2012I replace our aging rv082 routers with wireless rv220w routers. The gateway to gateway vpn works great, however I am no longer able to manage our print servers port 80 management page. I can ping any host with success, and I can manage hosts that have a port 10000 or 8000 web interface - but no port 80 ones.. After effects tracking. I had no issues when using the old rv082 routers..
Cisco Routers :: RV220W Gateway-to-Gateway Inter VLAN Routing?
Jul 6, 2012I picked up a pair of RV220W's and before I spent loads of time at a remote site, I figured I'd go through some VPN testing at home to make sure I could get it setup properly. What this means is I've plugged the Internet uplink into a switch, then from the switch into both routers & configured them (using unique static IP's for each) from there. For what its worth: While I have some IT experience, I don't have strong networking experience.
I setup several VLAN's on the local RV220W, and the end result is to make it so that an asset at the remote site with an IP in any of the ranges (192.168.121.0/24, 192.168.131.0/24, 192.168.141.0/24 and any future VLANs) can communicate with/access resouces at the local site. Likewise, an asset at the local site with an IP in any of the ranges (.121, .131, .141 + any future VLANs) should be able to reach the remote resources (currently just 192.168.181.0/24, but future VLANs as well).
This evening I tried to focus on the relevant VPN pages of the Administration Guide to get the VPN up. Leaving the defaults I got as far as establishing a link between both sites and it seems that things are working right: From the remote site (.181) I can access the local site (.121, .131, .141); and from the local site I can at least ping resources (a laptop) on the remote site. (Yay!)
However, when I physically connected an asset that had a 192.168.121.X, 192.168.131.X and 192.168.141.X IP addresses to the remote RV220W (which is 192.168.181.0/24), I couldn't see it from the remote or local sites.I assume this is expected. But I'm reaching out to the community to see what other possibilities might be available becuase networking is a weak area for me. I figured it might be something like a Static [or Dynamic] Route but I really am not 100% sure.
'TECHNICAL' SPECS
Local Router LAN/WAN Settings:
LAN IP: 192.168.121.1 on default VLAN (1)
VLAN 13 defined 192.168.131.1 with DHCP enabled; Reservations created outside of DHCP scope
VLAN 14 defined 192.168.141.1 with DHCP enabled, Reservations created outside of DHCP scope
Inter VLAN Routing enabled for all VLANs
[URL]
Cisco Routers :: RVS4000 To Use A Gateway To Gateway IPSec Tunnel
Oct 17, 2011Can I have use a Gateway-to-Gateway IPSec tunnel whereby a user can surf the Internet using his local Internet connection and at the same time connect through the IPSec tunnel to a remote subnet using RVS4000 routers?
Cisco Routers :: RV016 Gateway To Gateway RV082 Won't Connect
Mar 9, 2012New hardware here, requesting a bit of your knowledge, We are tryingin to setup a simple gateway to gateway VPN
HomeA Has an RV016 with a public static IP
Local Group Security Gateway type is IP Only with the IP
Local Security Group Type is Subnet, with the local IP class 192.160.0.0
Remote Security Gateway Type: Dynamic + Email
Email address some@emailaddress.com
Remote Security Group Type: Subnet
IP Address 192.168.1.0
IPSec Setup as default with nice password.
HomeB has an RV082 with a dynamic ADSL link
Local Group Security Gateway type is DynamicIP +Email
Email address some@emailaddress.com
Local Security Group Type is Subnet, with the local IP class 192.160.1.0
Remote Security Gateway Type: IP Only
Remote Security Group Type: Subnet
IP Address 192.168.0.0
IPSec Setup as default with nice password.
The idea is for HomeB which has a dynamic IP, to reach HomeA, which has a static IP and connect. But they just wont. I have not clue what's wrong, I followed the instructions, maybe i miss interpreted something. I could share the VPN logs for both., Im getting a lot of errors there.
Cisco Routers :: Getting VPN Gateway To Gateway With NAT For Multiple Subnets / RV082?
Feb 11, 2012I have a pair of RV082 routers and I'd like to configure gateway to gateway VPN tunnel as described in a cookbook, 'How to configure a VPN tunnel that routes all traffic to the Remote Gateway,' (file name Small_business_router_tunnel_Branch_to_Main.doc). I followed this cookbook and found that my while the Main office has internet connectivity, the branch subnet doesn't have internet connectivity.
Routing does behave as advertised, where all traffic does go to the main office. However, the 192.168.1.0 subnet in the branch office does not get internet connectivity. I've read in other posts that the Main office router will only provide NAT for the local subnet, not the branch office subnet. Is there a way to configure the RV082 router to provide NAT for all subnets?
If not, which Cisco product will provide the VPN Tunnel connectivity as well as the NAT for all subnets? Can the RV082 be used as part of the final solution or are my RV082s a wasted expenditure?
Following is the configuration that I'd implemented, (real IP and IKE keys are bogus).
Gateway To Gateway
Remote Main Office
Add a New Tunnel
Tunnel No. 1 2
Tunnel Name : n1-2122012_n2-1282012 n1-2122012_n2-1282012
Interface : WAN1 WAN1
[code]...
Cisco Routers :: RV8082 Setup A VPN Tunnel With Gateway-to-Gateway
Client To Gateway Vpn Rv042 Review
Apr 8, 2012I have two Cisco RV8082 Routers which I would like to setup a VPN Tunnel with Gateway to Gateway. One location is a static IP Address. The other location is a dynamic IP address.
Cisco Routers :: RV042 QuickVPN / Gateway Not Responding
Jun 28, 2011I have router Linksys RV042 v1.2 with latest firmware Version: 1.3.13.02-tm. And I'm using QuickVPN v 1.4.1.2. I've setup VPN connection with values, below: But every time I'm trying to connect to router by VPN it always popup a window 'Remote Gateway not responding'.It occurs when I'm trying to connect to VPN behind other router, when I'm connected directly to Internet the connection is established.But I'm connecting to other networks using VPN and it's working properly (behind the same router), so I think it's problem with RV042 configuration but I don't now weher.

